Auto-generate Flow Chart from Java/C++ Codes:
Raptor Flowchart Tutorial For Beginners
Tuesday, November 27, 2012
Simple Way To Practice SQL Online
Cara Mudah Untuk Belajar Praktis SQL Secara Online
1) http://sqlfiddle.com
2) http://sqlzoo.net
3) http://apex.oracle.com (Oracle)
Labels:
Cara Mudah Untuk...,
database,
mysql,
oracle,
Simple Way To...
Monday, November 26, 2012
Simple Way Draw Computer Network Diagram
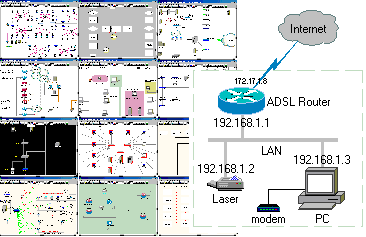
Cara Mudah Melukis Diagram Rangkaian Komputer
| |
Network Notepad is a freeware app for creating interactive network diagrams. | |
Simple Way To Learn Linux Commands Using Online Terminal
Cara Mudah Belajar Linux Commands Melalui Online Terminal
Cara Mudah Belajar Arahan Linux Melalui Terminal Atas Talian
Jika anda hanya sekadar mahu mencuba-cuba sebahagian kecil arahan UNIX/LINUX, anda tidak perlu memasang LINUX pada komputer anda, anda boleh menggunakan terminal di pautan berikut, http://www.masswerk.at/jsuix/.
Apabila anda klik pautan di atas, anda akan melihat paparan di bawah. Klik pada teks >Open Terminal untuk memulakan sessi terminal.
Anda boleh rujuk koleksi arahan UNIX/LINUX di pautan berikut: http://cb.vu/unixtoolbox.xhtml (Tidak semua arahan ini boleh dilaksanakan melalui terminal di atas)
Simple Way To Install Ubuntu Linux On Virtual Machine
Cara Mudah Memasang Ubuntu Linux Ke Atas Virtual Machine
Cara Mudah Memasang Ubuntu Linux Ke Atas Mesin Maya
Mencuba Sistem Operasi Linux adalah sesuatu yang menarik. Bagi pengguna biasa, ia memberi pengalaman menggunakan komputer melalui sistem operasi alternatif (kita sudah biasa dengan Microsoft Windows dan adakalanya kita ingin tahu apakah ada cara lain yang lebih baik daripada cara Microsoft Windows mengendalikannya). Bagi pengguna yang advanced, pengalaman menggunakan Linux memberikan kelebihan daya saing dalam kemahiran komputer kerana sebahagian komputer server dikawal melalui Sistem Operasi Linux.
Antara Sistem Linux yang popular adalah Redhat (atau pengikutnya seperti Centos dan Oracle Linux) dan Ubuntu (yang pernah juga digelar Sistem Linux yang ramah pengguna).
Artikel di bawah memberi panduan langkah-langkah mudah memasang Ubuntu Linux ke komputer anda tanpa perlu mengubah apa-apa setting sedia ada pada Windows anda. Kaedah yang menggunakan perisian VirtualBox ini digelar Virtualization.
Panduan ini disalin dari: http://www.bjorn3d.com/2009/06/how-to-run-linux-in-a-virtual-desktop/#.ULN-XIeyAlo
========================================================================
Have you ever wanted to install Linux, just to see what its like without actually setting up a dual boot? Or maybe you’d just like to try Folding@Home from a Linux install. Read on as we show you how to set up a Virtual PC from within Windows.
VIRTUAL PC – WHAT IT IS
Virtual PC has been around for some time now, with the latest version being Virtual PC 2007. While the term virtual machine thrown around a bit, it’s important to make the distinction: Virtual PC creates a virtual machine on your computer, but Virtual PC is the software created by Microsoft to perform that task. Some will be surprised to hear that Virtual PC is free, the full download is available from Microsoft’s website.
There are a few issues to note when preparing to Install Virtual PC:
First, ensure that you have the correct version of Windows installed. According to the download page over atwww.microsoft.com, Virtual PC will run on Vista Business/Enterprise/Ultimate, Windows Server 2003 Standard Edition, Windows XP Professional, or Windows XP Tablet PC Edition. They make no mention of any of the Home editions of Windows.
Second, you must take into consideration the hardware requirements, the RAM and disk space needs for both the host operating system and the system you run in Virtual PC must be added together to determine your total system requirements. Don’t worry however, as you can get Linux installs that take up very little space and require little overhead.
Lastly, don’t worry too much about processor speed. According to the requirements listed by Microsoft, Virtual PC 2007 will run on AMD Athlon/Duron or Intel Celeron/Pentium II processors. Essentially, if your processor can handle XP or Vista, you’re good to go with the CPU requirement.
VIRTUALBOX – THE COMPETITION
VirtualBox is Sun Microsystem’s answer to VirtualPC. Their version is also free and unlike Virtual PC 2007, it is published under the GNU General Public License. For those of you that don’t know, this means that not only do you get the program for free, but the source code is available as well, just like Linux. This is handy because the general public can alter the source code to offer improvements or fix bugs for their specific application.
VIRTUAL MACHINE – WHY BOTHER?
Some of you are already asking, I’m sure, why you would need to install a virtual machine. The answers are many and varied but I can think of a few very good ones. I, for example, found Virtual PC when taking a class at the local college. For our class we needed to install Linux just to get some experience with it. The college I attend however, does not have PC’s dedicated for any one class and installing a dual-boot or single-boot Linux setup was out of the question. Our instructor led us instead to Microsoft’s website to download Virtual PC and we had Linux up and running in about an hour, and then were able to simply delete the Linux install and uninstall Virtual PC when it was time to leave.
Another reason that many people install Linux in a virtual machine is to run a program called Folding@Home. This software, for those of you that have not heard about it yet, is a project started at Stanford University to research protein folding and the way that it relates to different diseases such as Parkinson’s, Alzheimer’s, cancer, and many others. The way it works is simple, you download a “work unit” from Stanford’s servers and your PC uses it’s idle cycles (time the CPU is sitting idle) to compute and simulate the protein folding. Once the work unit is finished, it sends the results back to Stanford for analysis, more info can be found here. If you’re interested in folding for the Bjorn3D.com team, use the team number 41608 when you set up your client. The reason that people like to use Linux to do the work is one of speed. The Linux client, for some time, was much faster than the Windows client. With the GPU client that has been released, that has largely been overcome because Linux does not have a GPU client yet. However, the list of supported GPU’s is still fairly short and if you do not have one on the list, you’re stuck with the CPU client, which runs faster in Linux.
Finally, for people like me, it allows you another way to tinker with your PC. The great thing, perhaps the greatest thing, about Virtual PC is that you can tinker all you want, and you’re not going to permanently alter your computer. This is especially nice because every Operating System around requires its own HDD partition, Virtual PC simply creates a folder on your hard drive instead of an actual partition, but the virtual machine sees it as a partition.
VIRTUAL MACHINE – INSTALLATION
Installing Virtual PC, or VirtualBox for that matter is simple. The first step, of course, is to go get it, click here for the Virtual PC 2007 download page or here for the VirtualBox site. Once you’ve got it downloaded simply run the file, choose a destination location and off you go! It’s a fast, simple installation.
Today we will guide you through the VirtualBox installation. The reasons for choosing Sun’s solution over Microsoft’s is simple, it works. I tried Virtual PC 2007 first, and there are other guides out there with command line parameters to add to your Linux install to make it work. I tried their solutions which just raised other problems, then I tried VirtualBox. It installed correctly, the first time, with little to no specialized knowledge of Linux. Read on to see just how easy Sun has made it…
VIRTUALBOX – INSTALLATION
Installing VirtualBox is simple. The first step, of course, is to go get it, click here for the download page. Once you’ve got it downloaded simply run the file, choose a destination location and off you go! It’s a fast, simple installation.
Once you’ve got that taken care of you’re presented with this screen:
From here the process is fairly straightforward, at least to get started. Click on the “New” button, represented by the blue gear. This will bring up the “Create New Virtual Machine” Wizard. When that wizard starts you are presented first with a brief welcome page, simply click next and it will take you to the Virtual Machine (VM) and Operating System (OS) Type screen. For this article we will be working with Ubuntu 9.04, which is Ubuntu’s latest release. It’s free and you can get it here. They offer Desktop, Server, and Netbook editions.
On the next screen you need to set the amount of RAM that will be available to your Guest Operating System (Linux). Check to see how much memory your Host Operating System (Windows) uses, do a little math and figure out how much you can get away with using. If you’re going to be running a lot of programs, or F@H for instance, make sure you allocate AT LEAST 512MB of RAM. I prefer a little headroom, so I’ll set mine at 768MB.
Next comes the HDD setup. This is the great thing about Virtual Machines, rather than partition your drive and destroy data, it will create a file the size of your Virtual Hard Disk and simply write to and from that “drive.” On the next screen, select “Create new hard disk” and make sure you check the “Primary Master” box then click next.
The next screen is just an intro to the next wizard, the “Create New Virtual Disk” wizard. Click next.
Here you have a choice. Fixed-size is just that, and they do a pretty good job of explaining it. The “dynamically expanding storage” is an interesting feature, you can set a disk to the size you need just for the install and as your Guest OS grows the file that it creates as the Virtual Drive will grow with it (up to a certain size, which you set). For this tutorial we’ll stick with the Fixed-size storage, adding as few variable as possible into the mix.
Next you set a location for your Virtual Drive on your physical disk. Just click the browse button and away you go. You can set it on an external HDD, USB thumb drive, or in my case a 900GB partition. After that set the size of your Virtual Disk (20GB is more than big enough for a Ubuntu install) and click next.
Check over your options on the summary page one last time, click finish and you’re all done with the disk setup. After you click finish the program will setup the file which could take a while, depending on the size that you set your Virtual Drive to. It will format the file so that your Guest OS will see it as an actual HDD partition.
Once VirtualBox is done setting everything up you’re presented with a summary page. Review everything one more time, click finish.
Now that the wizard is all finished, you’re presented with the overview below. Let’s cover a few things and then get started with the installation. You have the option now to set the amount of video memory your Guest OS will use, up to 128MB. Your CD/DVD-ROM can be mounted for use by the OS, or you can create a virtual drive so that it can use .iso files as CD/DVD disks. Don’t worry about the network settings, it is configured to use your Host network and pass it through to the Guest OS so your internet will work on the first boot. Set some shared folders if you like, to allow you to pass files between your Host and Guest OS’s.
Now click the green start arrow and let’s get to installing!
UBUNTU – INSTALLATION
After you click start you’re presented with another wizard. This one is convenient because unlike modifying a BIOS it’s quite straightforward. For our purposes select “CD/DVD-ROM Device” and then either “Host Drive” and the path to your physical optical drive, or “Image File”. Click next.
If you chose to install from an image file, as I did, you’re presented with the Images screen, simply click add, browse to your image file and it will populate in the box, click select at the bottom of the screen to boot from that image.
And we get another summary page, with a little advice about unmounting the image as well. After you click finish VirtualBox will start your Guest machine, you will see it go through a short boot process and then you start the installation, for real this time.
After a successful boot you are presented with a plethora of languages to choose from, I think I’ll stick with English.
Here is where Virtual PC and VirtualBox part ways. Up until this point the install is fairly similar. If we were using virtual PC, we’d have to press F4 and select “Safe Graphics Mode” and then press F6 to add command line parameters. Then we’d select “Try Ubuntu…” boot into the Live CD environment and then click install Ubuntu. We’d then have to reset the box, add command-line parameters to the GRUB loader, and then cross our fingers and hope that it works.
With VirtualBox however, skip all the other stuff and just click “Install Ubuntu.” Really, is it hard to see why we went with VirtualBox instead?
UBUNTU – INSTALLATION CONT.
Okay, now for the GUI version of the installer. Things have changed a lot in the ten years since I last tried Linux. This process from this point forward is completely GUI driven, meaning Graphical User Interface for those of you that are new to this. What that means is that you don’t have to memorize a lot of command line functions and parameters, as it’s all a mouse-click away.
First comes the language select, again, just in case you decided after the initial boot-up that you’d rather speak Swahili.

Pick a time zone, any time zone! My clock was off pretty significantly here, you can adjust it later.

You can choose any keyboard imaginable. I prefer the one that matches my keyboard, but it’s up to you.

Remember that Virtual Disk you set up earlier? I promised the Guest OS would see it as a real HDD, didn’t I? Now you can even partition it further, should you choose to. I prefer one big one for Virtual Machines, for simplicity’s sake.

Now you need to set up a user-account. Always require a password to log in, it’s a good habit to have.

Yes, I noticed too that the install procedure goes from Step 5 to Step 7. I don’t know where step 6 is, maybe it’s only in the server edition? I don’t know, but we seem to have done okay without it. Review your install settings, just in case. Notice that even with one partition set up, it gives us ext3 and swap. This is a Linux thing, not a VirtualBox thing. Click Install to proceed and it will run through the formatting and installation procedure as if it were a stand-alone install. Then it will ask you to reboot.

UBUNTU – FINISHING UP
Okay, remember when I mentioned unmounting the image? This is why, upon rebooting it will just load the CD image again and again wanting you to reinstall the program and you’ll probably be wondering what happened. I clicked “Unmount CD/DVD-ROM” and rebooted again, that didn’t work so…

…I clicked “Mount CD/DVD-ROM,” clicked on CD/DVD-ROM Image and removed the image from the list. When I rebooted again it still didn’t work, so I told the Virtual Machine to shut down and close, then restarted it and it went right into the GRUB loader, booting immediately into our fresh Linux install. Now you know…

And on that note, we’re at the login screen. Simply login and you’ve got a new, fully functional version of Linux without the hassle or drama of partitioning/formatting/multi-booting your home system.

THE VIRTUAL MACHINE – FINAL THOUGHTS
There are a few things you need to keep in mind. First of all, while your Guest OS will be fully functional, it does require system resources beyond that of most programs. Consider this, you’re running an entire operating system within an operating system.
I’d like to make it clear that Virtual PC is a good program, but it was not designed with Linux in mind. Hence the little idiosyncracies when trying to Install Ubuntu. If you’d like to install a different version of Windows in a virtual machine, it’ll work quite well. For virtual Linux machines however, I simply have to recommend Sun’s VirtualBox due to its out of the box functionality.
Linux has become much more straightforward over the last few years, drawing a bigger user-base than it’s ever had. That said, it is still a relatively small community. Most of your questions about Linux can be answered somewhere on the Web. Like many of you reading this guide, I am fairly new to Linux. I’ve dabbled in it from time to time, but never gotten deeply involved in it. That is changing however, any questions you have on the subject can be directed to our forums where I and our members will do the best we can to answer them. That said, if you’re a Linux expert, come join us and share your experience!
Simple Way To Reset Oracle Database SYSTEM Password
Cara Mudah Untuk Reset Oracle Database SYSTEM Password
Sudah menjadi kelaziman, para administrator kadang-kadang terlupa password yang dibuat untuk SYSTEM (SYS dan SYSDBA) bagi Oracle Database.
Blog berikut memberikan panduan menghadapinya bagi:
1) Sistem Linux
2) Sistem Windows
=======================================================
SISTEM LINUX
sumber: http://rolfje.wordpress.com/2007/01/16/lost-oracle-sys-and-system-password/
Lost Oracle SYS and SYSTEM password?
If your administration is as good as anybodies, you are bound to loose the not-so-frequently used password for the SYS and SYSTEM users of oracle. Here are a few ways I found to re-set those passwords:
Method 1: SQLPLUS (Tested on AIX Oracle 9.2.0.1.0)
Log into the database server as a user belonging to ‘dba’ [unix ] or ‘ora_dba’ [windows ] group , typically ‘oracle’, or an administrator on your windos machine. You are able to log into Oracle as SYS user, and change the SYSTEM password by doing the following:
Method 2: Creating pwd file (Tested on Windows Oracle 8.1.7)
Method 1: SQLPLUS (Tested on AIX Oracle 9.2.0.1.0)
Log into the database server as a user belonging to ‘dba’ [unix ] or ‘ora_dba’ [windows ] group , typically ‘oracle’, or an administrator on your windos machine. You are able to log into Oracle as SYS user, and change the SYSTEM password by doing the following:
$ sqlplus "/ as sysdba" SQL*Plus: Release 9.2.0.1.0 - Production on Mon Apr 5 15:32:09 2004 Copyright (c) 1982, 2002, Oracle Corporation. All rights reserved. Connected to: Oracle9i Enterprise Edition Release 9.2.0.1.0 - Production With the OLAP and Oracle Data Mining options JServer Release 9.2.0.1.0 - Production SQL> show user USER is "SYS" SQL> passw system Changing password for system New password: Retype new password: Password changed SQL> quitNext, we need to change the password of SYS:
$ sqlplus "/ as system" SQL*Plus: Release 9.2.0.1.0 - Production on Mon Apr 5 15:36:45 2004 Copyright (c) 1982, 2002, Oracle Corporation. All rights reserved. SP2-0306: Invalid option. Usage: CONN[ECT] [logon] [AS {SYSDBA|SYSOPER}] whereYou should now be able to log on the SYS and SYSTEM users, with the passwords you just typed in.::= Connected to: Oracle9i Enterprise Edition Release 9.2.0.1.0 - Production With the OLAP and Oracle Data Mining options JServer Release 9.2.0.1.0 - Production SQL> passw sys Changing password for sys New password: Retype new password: Password changed SQL> quit[/ ][@ ] | / Enter user-name: system Enter password:
Method 2: Creating pwd file (Tested on Windows Oracle 8.1.7)
- Stop the Oracle service of the instance you want to change the passwords of.
- Find the PWD###.ora file for this instance, this is usuallly located atC:\oracle\ora81\database\, where ### is the SID of your database.
- rename the PWD###.ora file to PWD###.ora.bak for obvious safety reasons.
- Create a new pwd file by issuing the command:
orapwd file=C:\oracle\ora81\database\PWD###.ora password=XXXXX
where ### is the SID and XXXXX is the password you would like to use for the SYS and INTERNAL accounts. - Start the Oracle service for the instance you just fixed. You should be able to get in with the SYS user and change other passwords from there.
=======================================================
SISTEM WINDOWS
sumber: http://www.componentworkshop.com/blog/2009/05/07/oracle-reset-forgottenunknown-system-password
If you have forgotten the SYSTEM password for an Oracle Database Server, you can reset it by logging in to Windows as Administrator and connecting to Oracle as sysdba. This tip explains how.
Great Book
For this to work you must be logged in to the Windows Server that is running Oracle as Administrator. Here are the steps to reset the password:
Start SQL*Plus (Start -> Programs -> Oracle – Instance Name -> Application Development -> SQL Plus).
At the login prompt, in the user-name field, type ”/as sysdba” (including the forward slash, but without the quotes). Click OK.
You are now connected as system with full DBA rights.
To reset the password of the SYSTEM password (or any other user password), run the following query:
alter user system identified by NewPasswordHere;
Change the password to whatever you want it to be. Note also that it doesn't need to be in single quotes, as you might expect. Hit ENTER to run the query and you should receive positive affirmation of the change:
“User altered.”
If you don't have SQL*Plus (for example, if you are using Oracle XE), open a console (Start -> Run -> type 'cmd.exe' followed by and then run sqlplus from the command line:
sqlplus / as sysdba
Once connected, use alter user as described above.
Apart from the more obvious uses, this tip is particularly useful if you’ve imported a database dump from another server and don’t know the system password.
Sunday, November 25, 2012
How Internet Infrastructure Works
Bagaimana Infrastruktur Internet Berfungsi
by Jeff Tyson
Browse the article How Internet Infrastructure Works
Introduction to How Internet Infrastructure Works
One of the greatest things about the Internet is that nobody really owns it. It is a global collection of networks, both big and small. These networks connect together in many different ways to form the single entity that we know as the Internet. In fact, the very name comes from this idea of interconnected networks.
Since its beginning in 1969, the Internet has grown from four host computer systems to tens of millions. However, just because nobody owns the Internet, it doesn't mean it is not monitored and maintained in different ways. The Internet Society, a non-profit group established in 1992, oversees the formation of the policies and protocols that define how we use and interact with the Internet.
In this article, you will learn about the basic underlying structure of the Internet. You will learn about domain name servers, network access points and backbones. But first you will learn about how your computer connects to others.
 When you connect to the Internet, your computer becomes part of a network.
When you connect to the Internet, your computer becomes part of a network.
The Internet: Computer Network Hierarchy
Every computer that is connected to the Internet is part of a network, even the one in your home. For example, you may use a modem and dial a local number to connect to an Internet Service Provider (ISP). At work, you may be part of a local area network (LAN), but you most likely still connect to the Internet using an ISP that your company has contracted with. When you connect to your ISP, you become part of their network. The ISP may then connect to a larger network and become part of their network. The Internet is simply a network of networks.
Most large communications companies have their own dedicated backbones connecting various regions. In each region, the company has a Point of Presence(POP). The POP is a place for local users to access the company's network, often through a local phone number or dedicated line. The amazing thing here is that there is no overall controlling network. Instead, there are several high-level networks connecting to each other through Network Access Points or NAPs.
Internet Network Example
Here's an example. Imagine that Company A is a large ISP. In each major city, Company A has a POP. The POP in each city is a rack full of modems that the ISP's customers dial into. Company A leases fiber optic lines from the phone company to connect the POPs together (see, for example, this UUNET Data Center Connectivity Map).
Imagine that Company B is a corporate ISP. Company B builds large buildings in major cities and corporations locate their Internet server machines in these buildings. Company B is such a large company that it runs its own fiber optic lines between its buildings so that they are all interconnected.
In this arrangement, all of Company A's customers can talk to each other, and all of Company B's customers can talk to each other, but there is no way for Company A's customers and Company B's customers to intercommunicate. Therefore, Company A and Company B both agree to connect to NAPs in various cities, and traffic between the two companies flows between the networks at the NAPs.
In the real Internet, dozens of large Internet providers interconnect at NAPs in various cities, and trillions of bytes of data flow between the individual networks at these points. The Internet is a collection of huge corporate networks that agree to all intercommunicate with each other at the NAPs. In this way, every computer on the Internet connects to every other.
The Function of an Internet Router
All of these networks rely on NAPs, backbones and routers to talk to each other. What is incredible about this process is that a message can leave one computer and travel halfway across the world through several different networks and arrive at another computer in a fraction of a second!
The routers determine where to send information from one computer to another. Routers are specialized computers that send your messages and those of every other Internet user speeding to their destinations along thousands of pathways. A router has two separate, but related, jobs:
- It ensures that information doesn't go where it's not needed. This is crucial for keeping large volumes of data from clogging the connections of "innocent bystanders."
- It makes sure that information does make it to the intended destination.
In performing these two jobs, a router is extremely useful in dealing with two separate computer networks. It joins the two networks, passing information from one to the other. It also protects the networks from one another, preventing the traffic on one from unnecessarily spilling over to the other. Regardless of how many networks are attached, the basic operation and function of the router remains the same. Since the Internet is one huge network made up of tens of thousands of smaller networks, its use of routers is an absolute necessity. For more information, read How Routers Work.
Internet Backbone
The National Science Foundation (NSF) created the first high-speed backbone in 1987. Called NSFNET, it was a T1 line that connected 170 smaller networks together and operated at 1.544 Mbps (million bits per second). IBM, MCI and Merit worked with NSF to create the backbone and developed a T3 (45 Mbps) backbone the following year.
Backbones are typically fiber optic trunk lines. The trunk line has multiple fiber optic cables combined together to increase the capacity. Fiber optic cables are designated OC for optical carrier, such as OC-3, OC-12 or OC-48. An OC-3 line is capable of transmitting 155 Mbps while an OC-48 can transmit 2,488 Mbps (2.488 Gbps). Compare that to a typical 56K modem transmitting 56,000 bps and you see just how fast a modern backbone is.
Today there are many companies that operate their own high-capacity backbones, and all of them interconnect at various NAPs around the world. In this way, everyone on the Internet, no matter where they are and what company they use, is able to talk to everyone else on the planet. The entire Internet is a gigantic, sprawling agreement between companies to intercommunicate freely.
Internet Protocol: IP Addresses
Every machine on the Internet has a unique identifying number, called an IP Address. The IP stands for Internet Protocol, which is the language that computers use to communicate over the Internet. A protocol is the pre-defined way that someone who wants to use a service talks with that service. The "someone" could be a person, but more often it is a computer program like a Web browser.
A typical IP address looks like this:
To make it easier for us humans to remember, IP addresses are normally expressed in decimal format as a dotted decimal number like the one above. But computers communicate in binary form. Look at the same IP address in binary:
The four numbers in an IP address are called octets, because they each have eight positions when viewed in binary form. If you add all the positions together, you get 32, which is why IP addresses are considered 32-bit numbers. Since each of the eight positions can have two different states (1 or zero), the total number of possible combinations per octet is 28 or 256. So each octet can contain any value between zero and 255. Combine the four octets and you get 232 or a possible 4,294,967,296 unique values!
Out of the almost 4.3 billion possible combinations, certain values are restricted from use as typical IP addresses. For example, the IP address 0.0.0.0 is reserved for the default network and the address 255.255.255.255 is used for broadcasts.
The octets serve a purpose other than simply separating the numbers. They are used to create classes of IP addresses that can be assigned to a particular business, government or other entity based on size and need. The octets are split into two sections: Net and Host. The Net section always contains the first octet. It is used to identify the network that a computer belongs to. Host (sometimes referred to as Node) identifies the actual computer on the network. The Host section always contains the last octet. There are five IP classes plus certain special addresses. You can learn more about IP classes at What is an IP address?.
Internet Protocol: Domain Name System
When the Internet was in its infancy, it consisted of a small number of computers hooked together with modems and telephone lines. You could only make connections by providing the IP address of the computer you wanted to establish a link with. For example, a typical IP address might be 216.27.22.162. This was fine when there were only a few hosts out there, but it became unwieldy as more and more systems came online.
The first solution to the problem was a simple text file maintained by the Network Information Center that mapped names to IP addresses. Soon this text file became so large it was too cumbersome to manage. In 1983, the University of Wisconsin created the Domain Name System (DNS), which maps text names to IP addresses automatically. This way you only need to remember www.howstuffworks.com, for example, instead of HowStuffWorks.com's IP address.
URL: Uniform Resource Locator
When you use the Web or send an e-mail message, you use a domain name to do it. For example, the Uniform Resource Locator (URL) "http://www.howstuffworks.com" contains the domain name howstuffworks.com. So does this e-mail address: example@howstuffworks.com. Every time you use a domain name, you use the Internet's DNS servers to translate the human-readable domain name into the machine-readable IP address. Check out How Domain Name Servers Work for more in-depth information on DNS.
Top-level domain names, also called first-level domain names, include .COM, .ORG, .NET, .EDU and .GOV. Within every top-level domain there is a huge list of second-level domains. For example, in the .COM first-level domain there is:
- HowStuffWorks
- Yahoo
- Microsoft
Every name in the .COM top-level domain must be unique. The left-most word, like www, is the host name. It specifies the name of a specific machine (with a specific IP address) in a domain. A given domain can, potentially, contain millions of host names as long as they are all unique within that domain.
DNS servers accept requests from programs and other name servers to convert domain names into IP addresses. When a request comes in, the DNS server can do one of four things with it:
- It can answer the request with an IP address because it already knows the IP address for the requested domain.
- It can contact another DNS server and try to find the IP address for the name requested. It may have to do this multiple times.
- It can say, "I don't know the IP address for the domain you requested, but here's the IP address for a DNS server that knows more than I do."
- It can return an error message because the requested domain name is invalid or does not exist.
A DNS Example
Let's say that you type the URL www.howstuffworks.com into your browser. The browser contacts a DNS server to get the IP address. A DNS server would start its search for an IP address by contacting one of the root DNS servers. The root servers know the IP addresses for all of the DNS servers that handle the top-level domains (.COM, .NET, .ORG, etc.). Your DNS server would ask the root for www.howstuffworks.com, and the root would say, "I don't know the IP address for www.howstuffworks.com, but here's the IP address for the .COM DNS server."
Your name server then sends a query to the .COM DNS server asking it if it knows the IP address for www.howstuffworks.com. The DNS server for the COM domain knows the IP addresses for the name servers handling the www.howstuffworks.com domain, so it returns those.
Your name server then contacts the DNS server for www.howstuffworks.com and asks if it knows the IP address for www.howstuffworks.com. It actually does, so it returns the IP address to your DNS server, which returns it to the browser, which can then contact the server for www.howstuffworks.com to get a Web page.
One of the keys to making this work is redundancy. There are multiple DNS servers at every level, so that if one fails, there are others to handle the requests. The other key is caching. Once a DNS server resolves a request, it caches the IP address it receives. Once it has made a request to a root DNS server for any .COM domain, it knows the IP address for a DNS server handling the .COM domain, so it doesn't have to bug the root DNS servers again for that information. DNS servers can do this for every request, and this caching helps to keep things from bogging down.
Even though it is totally invisible, DNS servers handle billions of requests every day and they are essential to the Internet's smooth functioning. The fact that this distributed database works so well and so invisibly day in and day out is a testimony to the design. Be sure to read How Domain Name Servers Work for more information on DNS.
Internet Servers and Clients
Internet servers make the Internet possible. All of the machines on the Internet are either servers or clients. The machines that provide services to other machines are servers. And the machines that are used to connect to those services are clients. There are Web servers, e-mail servers, FTP servers and so on serving the needs of Internet users all over the world.
When you connect to www.howstuffworks.com to read a page, you are a user sitting at a client's machine. You are accessing the HowStuffWorks Web server. The server machine finds the page you requested and sends it to you. Clients that come to a server machine do so with a specific intent, so clients direct their requests to a specific software server running on the server machine. For example, if you are running a Web browser on your machine, it will want to talk to the Web server on the server machine, not the e-mail server.
A server has a static IP address that does not change very often. A home machine that is dialing up through a modem, on the other hand, typically has an IP address assigned by the ISP every time you dial in. That IP address is unique for your session -- it may be different the next time you dial in. This way, an ISP only needs one IP address for each modem it supports, rather than one for each customer.
Ports and HTTP
Any server machine makes its services available using numbered ports -- one for each service that is available on the server. For example, if a server machine is running a Web server and a file transfer protocol (FTP) server, the Web server would typically be available on port 80, and the FTP server would be available on port 21. Clients connect to a service at a specific IP address and on a specific port number.
Once a client has connected to a service on a particular port, it accesses the service using a specific protocol. Protocols are often text and simply describe how the client and server will have their conversation. Every Web server on the Internet conforms to the hypertext transfer protocol (HTTP). You can learn more about Internet servers, ports and protocols by reading How Web Servers Work.
Networks, routers, NAPs, ISPs, DNS and powerful servers all make the Internet possible. It is truly amazing when you realize that all this information is sent around the world in a matter of milliseconds! The components are extremely important in modern life -- without them, there would be no Internet. And without the Internet, life would be very different indeed for many of us.
For more information on the structure of the Internet and related topics, check out the links on the next page.
Lots More Information
Related Articles
- How Domain Name Servers Work
- How Bits and Bytes Work
- How Web Servers Work
- How Routers Work
- How Routing Algorithms Work
- How LAN Switches Work
- How Ethernet Works
- How CGI Scripts Work
- How Firewalls Work
- How Home Networking Works
- What are IP Classes?
- What is a packet?
- Where are all the Internet domain names registered and maintained?
- How does a T1 line work?
- Quiz Corner: WiFi Quiz
More Great Links
- NetworkComputing.com: All About IP Addresses
- BIND - the software that implements most name servers
- Domain name registries around the world
- WhatIs.com Internet Terms
- The Original HTTP as defined in 1991
by Jeff Tyson
Browse the article How Internet Infrastructure Works
Introduction to How Internet Infrastructure Works
One of the greatest things about the Internet is that nobody really owns it. It is a global collection of networks, both big and small. These networks connect together in many different ways to form the single entity that we know as the Internet. In fact, the very name comes from this idea of interconnected networks.
Since its beginning in 1969, the Internet has grown from four host computer systems to tens of millions. However, just because nobody owns the Internet, it doesn't mean it is not monitored and maintained in different ways. The Internet Society, a non-profit group established in 1992, oversees the formation of the policies and protocols that define how we use and interact with the Internet.
In this article, you will learn about the basic underlying structure of the Internet. You will learn about domain name servers, network access points and backbones. But first you will learn about how your computer connects to others.

When you connect to the Internet, your computer becomes part of a network.
The Internet: Computer Network Hierarchy
Every computer that is connected to the Internet is part of a network, even the one in your home. For example, you may use a modem and dial a local number to connect to an Internet Service Provider (ISP). At work, you may be part of a local area network (LAN), but you most likely still connect to the Internet using an ISP that your company has contracted with. When you connect to your ISP, you become part of their network. The ISP may then connect to a larger network and become part of their network. The Internet is simply a network of networks.
Most large communications companies have their own dedicated backbones connecting various regions. In each region, the company has a Point of Presence(POP). The POP is a place for local users to access the company's network, often through a local phone number or dedicated line. The amazing thing here is that there is no overall controlling network. Instead, there are several high-level networks connecting to each other through Network Access Points or NAPs.
Internet Network Example
Here's an example. Imagine that Company A is a large ISP. In each major city, Company A has a POP. The POP in each city is a rack full of modems that the ISP's customers dial into. Company A leases fiber optic lines from the phone company to connect the POPs together (see, for example, this UUNET Data Center Connectivity Map).
Imagine that Company B is a corporate ISP. Company B builds large buildings in major cities and corporations locate their Internet server machines in these buildings. Company B is such a large company that it runs its own fiber optic lines between its buildings so that they are all interconnected.
In this arrangement, all of Company A's customers can talk to each other, and all of Company B's customers can talk to each other, but there is no way for Company A's customers and Company B's customers to intercommunicate. Therefore, Company A and Company B both agree to connect to NAPs in various cities, and traffic between the two companies flows between the networks at the NAPs.
In the real Internet, dozens of large Internet providers interconnect at NAPs in various cities, and trillions of bytes of data flow between the individual networks at these points. The Internet is a collection of huge corporate networks that agree to all intercommunicate with each other at the NAPs. In this way, every computer on the Internet connects to every other.
The Function of an Internet Router
All of these networks rely on NAPs, backbones and routers to talk to each other. What is incredible about this process is that a message can leave one computer and travel halfway across the world through several different networks and arrive at another computer in a fraction of a second!
The routers determine where to send information from one computer to another. Routers are specialized computers that send your messages and those of every other Internet user speeding to their destinations along thousands of pathways. A router has two separate, but related, jobs:
- It ensures that information doesn't go where it's not needed. This is crucial for keeping large volumes of data from clogging the connections of "innocent bystanders."
- It makes sure that information does make it to the intended destination.
In performing these two jobs, a router is extremely useful in dealing with two separate computer networks. It joins the two networks, passing information from one to the other. It also protects the networks from one another, preventing the traffic on one from unnecessarily spilling over to the other. Regardless of how many networks are attached, the basic operation and function of the router remains the same. Since the Internet is one huge network made up of tens of thousands of smaller networks, its use of routers is an absolute necessity. For more information, read How Routers Work.
Internet Backbone
The National Science Foundation (NSF) created the first high-speed backbone in 1987. Called NSFNET, it was a T1 line that connected 170 smaller networks together and operated at 1.544 Mbps (million bits per second). IBM, MCI and Merit worked with NSF to create the backbone and developed a T3 (45 Mbps) backbone the following year.
Backbones are typically fiber optic trunk lines. The trunk line has multiple fiber optic cables combined together to increase the capacity. Fiber optic cables are designated OC for optical carrier, such as OC-3, OC-12 or OC-48. An OC-3 line is capable of transmitting 155 Mbps while an OC-48 can transmit 2,488 Mbps (2.488 Gbps). Compare that to a typical 56K modem transmitting 56,000 bps and you see just how fast a modern backbone is.
Today there are many companies that operate their own high-capacity backbones, and all of them interconnect at various NAPs around the world. In this way, everyone on the Internet, no matter where they are and what company they use, is able to talk to everyone else on the planet. The entire Internet is a gigantic, sprawling agreement between companies to intercommunicate freely.
Internet Protocol: IP Addresses
Every machine on the Internet has a unique identifying number, called an IP Address. The IP stands for Internet Protocol, which is the language that computers use to communicate over the Internet. A protocol is the pre-defined way that someone who wants to use a service talks with that service. The "someone" could be a person, but more often it is a computer program like a Web browser.
A typical IP address looks like this:
To make it easier for us humans to remember, IP addresses are normally expressed in decimal format as a dotted decimal number like the one above. But computers communicate in binary form. Look at the same IP address in binary:
The four numbers in an IP address are called octets, because they each have eight positions when viewed in binary form. If you add all the positions together, you get 32, which is why IP addresses are considered 32-bit numbers. Since each of the eight positions can have two different states (1 or zero), the total number of possible combinations per octet is 28 or 256. So each octet can contain any value between zero and 255. Combine the four octets and you get 232 or a possible 4,294,967,296 unique values!
Out of the almost 4.3 billion possible combinations, certain values are restricted from use as typical IP addresses. For example, the IP address 0.0.0.0 is reserved for the default network and the address 255.255.255.255 is used for broadcasts.
The octets serve a purpose other than simply separating the numbers. They are used to create classes of IP addresses that can be assigned to a particular business, government or other entity based on size and need. The octets are split into two sections: Net and Host. The Net section always contains the first octet. It is used to identify the network that a computer belongs to. Host (sometimes referred to as Node) identifies the actual computer on the network. The Host section always contains the last octet. There are five IP classes plus certain special addresses. You can learn more about IP classes at What is an IP address?.
Internet Protocol: Domain Name System
When the Internet was in its infancy, it consisted of a small number of computers hooked together with modems and telephone lines. You could only make connections by providing the IP address of the computer you wanted to establish a link with. For example, a typical IP address might be 216.27.22.162. This was fine when there were only a few hosts out there, but it became unwieldy as more and more systems came online.
The first solution to the problem was a simple text file maintained by the Network Information Center that mapped names to IP addresses. Soon this text file became so large it was too cumbersome to manage. In 1983, the University of Wisconsin created the Domain Name System (DNS), which maps text names to IP addresses automatically. This way you only need to remember www.howstuffworks.com, for example, instead of HowStuffWorks.com's IP address.
URL: Uniform Resource Locator
When you use the Web or send an e-mail message, you use a domain name to do it. For example, the Uniform Resource Locator (URL) "http://www.howstuffworks.com" contains the domain name howstuffworks.com. So does this e-mail address: example@howstuffworks.com. Every time you use a domain name, you use the Internet's DNS servers to translate the human-readable domain name into the machine-readable IP address. Check out How Domain Name Servers Work for more in-depth information on DNS.
Top-level domain names, also called first-level domain names, include .COM, .ORG, .NET, .EDU and .GOV. Within every top-level domain there is a huge list of second-level domains. For example, in the .COM first-level domain there is:
- HowStuffWorks
- Yahoo
- Microsoft
Every name in the .COM top-level domain must be unique. The left-most word, like www, is the host name. It specifies the name of a specific machine (with a specific IP address) in a domain. A given domain can, potentially, contain millions of host names as long as they are all unique within that domain.
DNS servers accept requests from programs and other name servers to convert domain names into IP addresses. When a request comes in, the DNS server can do one of four things with it:
- It can answer the request with an IP address because it already knows the IP address for the requested domain.
- It can contact another DNS server and try to find the IP address for the name requested. It may have to do this multiple times.
- It can say, "I don't know the IP address for the domain you requested, but here's the IP address for a DNS server that knows more than I do."
- It can return an error message because the requested domain name is invalid or does not exist.
A DNS Example
Let's say that you type the URL www.howstuffworks.com into your browser. The browser contacts a DNS server to get the IP address. A DNS server would start its search for an IP address by contacting one of the root DNS servers. The root servers know the IP addresses for all of the DNS servers that handle the top-level domains (.COM, .NET, .ORG, etc.). Your DNS server would ask the root for www.howstuffworks.com, and the root would say, "I don't know the IP address for www.howstuffworks.com, but here's the IP address for the .COM DNS server."
Your name server then sends a query to the .COM DNS server asking it if it knows the IP address for www.howstuffworks.com. The DNS server for the COM domain knows the IP addresses for the name servers handling the www.howstuffworks.com domain, so it returns those.
Your name server then contacts the DNS server for www.howstuffworks.com and asks if it knows the IP address for www.howstuffworks.com. It actually does, so it returns the IP address to your DNS server, which returns it to the browser, which can then contact the server for www.howstuffworks.com to get a Web page.
One of the keys to making this work is redundancy. There are multiple DNS servers at every level, so that if one fails, there are others to handle the requests. The other key is caching. Once a DNS server resolves a request, it caches the IP address it receives. Once it has made a request to a root DNS server for any .COM domain, it knows the IP address for a DNS server handling the .COM domain, so it doesn't have to bug the root DNS servers again for that information. DNS servers can do this for every request, and this caching helps to keep things from bogging down.
Even though it is totally invisible, DNS servers handle billions of requests every day and they are essential to the Internet's smooth functioning. The fact that this distributed database works so well and so invisibly day in and day out is a testimony to the design. Be sure to read How Domain Name Servers Work for more information on DNS.
Internet Servers and Clients
Internet servers make the Internet possible. All of the machines on the Internet are either servers or clients. The machines that provide services to other machines are servers. And the machines that are used to connect to those services are clients. There are Web servers, e-mail servers, FTP servers and so on serving the needs of Internet users all over the world.
When you connect to www.howstuffworks.com to read a page, you are a user sitting at a client's machine. You are accessing the HowStuffWorks Web server. The server machine finds the page you requested and sends it to you. Clients that come to a server machine do so with a specific intent, so clients direct their requests to a specific software server running on the server machine. For example, if you are running a Web browser on your machine, it will want to talk to the Web server on the server machine, not the e-mail server.
A server has a static IP address that does not change very often. A home machine that is dialing up through a modem, on the other hand, typically has an IP address assigned by the ISP every time you dial in. That IP address is unique for your session -- it may be different the next time you dial in. This way, an ISP only needs one IP address for each modem it supports, rather than one for each customer.
Ports and HTTP
Any server machine makes its services available using numbered ports -- one for each service that is available on the server. For example, if a server machine is running a Web server and a file transfer protocol (FTP) server, the Web server would typically be available on port 80, and the FTP server would be available on port 21. Clients connect to a service at a specific IP address and on a specific port number.
Once a client has connected to a service on a particular port, it accesses the service using a specific protocol. Protocols are often text and simply describe how the client and server will have their conversation. Every Web server on the Internet conforms to the hypertext transfer protocol (HTTP). You can learn more about Internet servers, ports and protocols by reading How Web Servers Work.
Networks, routers, NAPs, ISPs, DNS and powerful servers all make the Internet possible. It is truly amazing when you realize that all this information is sent around the world in a matter of milliseconds! The components are extremely important in modern life -- without them, there would be no Internet. And without the Internet, life would be very different indeed for many of us.
For more information on the structure of the Internet and related topics, check out the links on the next page.
Lots More Information
Related Articles
- How Domain Name Servers Work
- How Bits and Bytes Work
- How Web Servers Work
- How Routers Work
- How Routing Algorithms Work
- How LAN Switches Work
- How Ethernet Works
- How CGI Scripts Work
- How Firewalls Work
- How Home Networking Works
- What are IP Classes?
- What is a packet?
- Where are all the Internet domain names registered and maintained?
- How does a T1 line work?
- Quiz Corner: WiFi Quiz
More Great Links
- NetworkComputing.com: All About IP Addresses
- BIND - the software that implements most name servers
- Domain name registries around the world
- WhatIs.com Internet Terms
- The Original HTTP as defined in 1991
Subscribe to:
Comments (Atom)



